Last updated 2020/04/17 1757 GMT+2
Week 1 Lecture
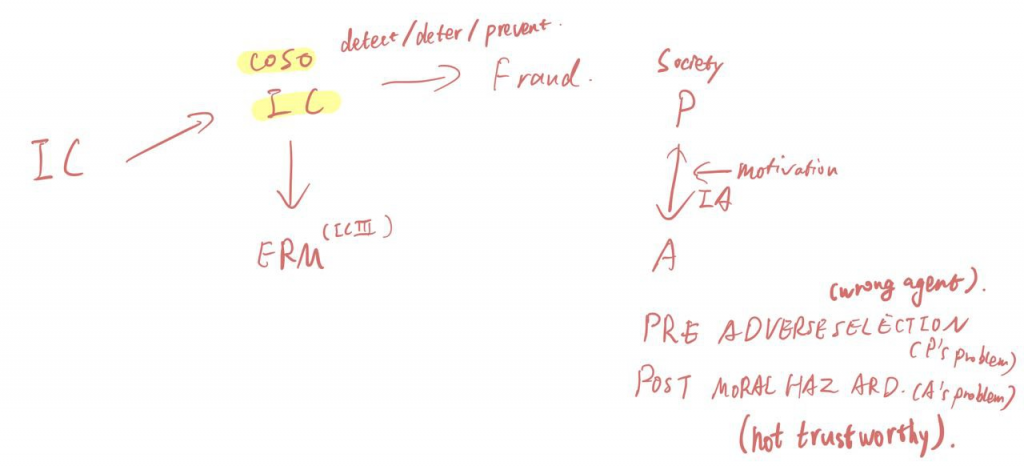
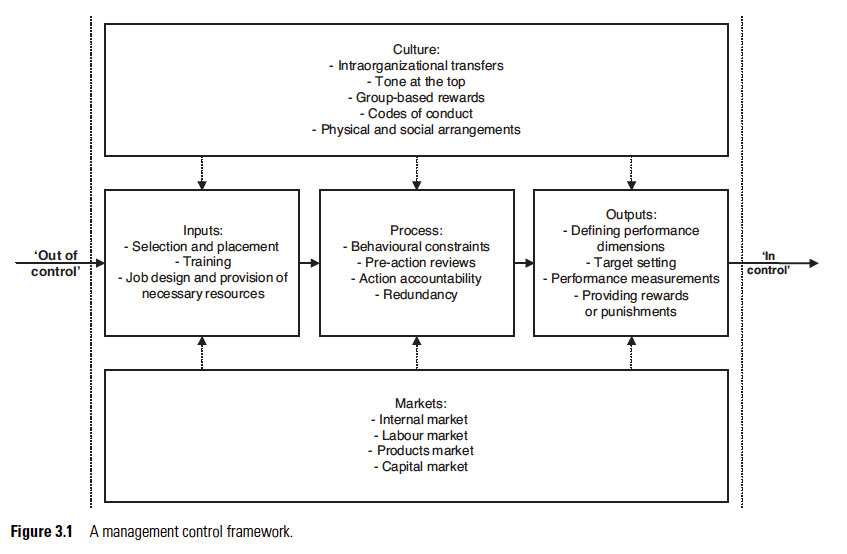
Control: To have reasonable assurance about the achievement of objectives.
Statistical risk management
Profit is the reward for accepting uncertainty.

Narrative One – Reliable information
The purpose of verification is to ensure the entries in the books are correct, and the reporting is reliable.
First change – Systemize
Audit-oriented approach: Audit trace/trail
Second change – Internal audit
Transaction -> Recording -> Verification
Narrative Two – Controlled performance
Fraud & ERM
Week 1 Tutorial
AIS: safeguard assets, reliable reporting, effective operations, compliance.
IC system: give reasonable assurance for AIS
↓
Recording <– Collecting
AIS: Transaction –> Collecting –> Recording –> Transforming (Decoding)
Spira & Page
Why IC changed in scope, nature and form.
However, nothing has changed. Systematically collecting, transforming and verifying data (transactinal –> system)
IC0
IC0 Internal check: Accountants to ensure transactional data are checked and verified before booking.
IC1
Financial information (reliable reporting)
Information technology (ERP): Collecting transactional data is far easier.
Transactional data become system data.
Is it possible to collect information about the procedures?
Third defense – Internal audit department: Audit trails (Documentation)
- Testing the system (control procedures)
- Verifying whether IC systems are in place and executed
Management accounting information (effectiveness and efficiency of operation, useful information)
Managerial practices –> Corporate governance
- Nobody trusts managers. (self-regulated)
- Ownership becomes anonymous (only interested in returns not operations).
Managers behave as owners as well.
Solution: Corporate governance regime
Internal auditors become monitors of the company.
CG codes require disclosures on IC and risk systems.
Risk management
Risks should be identified and mitigated.
Three streams of IC
- IC integrated frameworks (COSO)
- ERM (Enterprise Risk Management)
- Fraud
Fraud
Accountability should be monitored and verified.
Definition
- Lying: Fraudulent financial reporting
- Stealing: Misuse, abuse and theft
- Development of information makes it easier to detect fraud.
- Use of technology makes fraud more complex.
Week 2 Lecture
Accounting information system includes internal control.
COSO makes organizations more accountable on accounting information systems, i.e. making disclosures more verifiable.
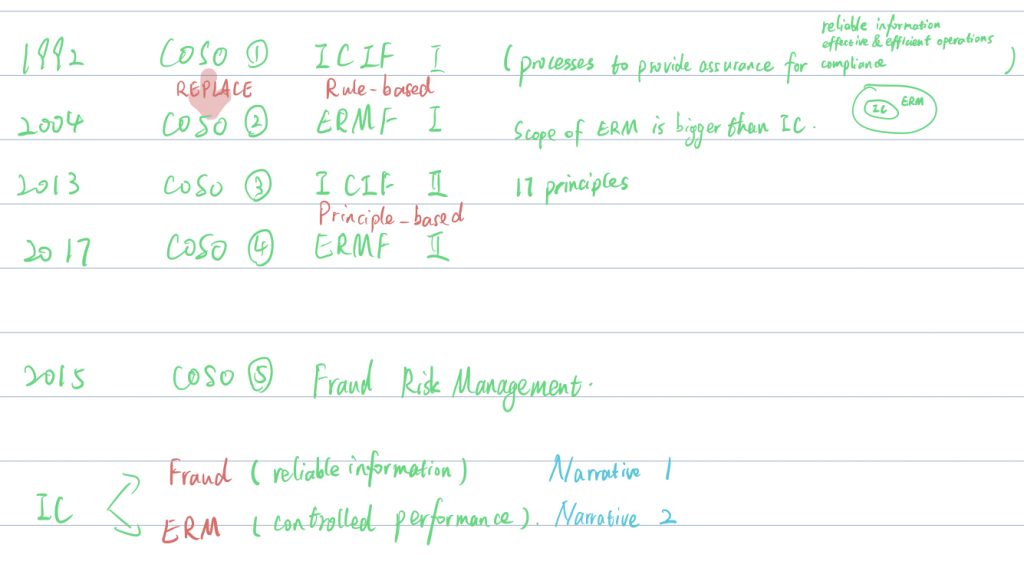
COSO 1 ICIF-1 Internal control integrated framework 1992
was replaced by
COSO 2 ERMF-1 Enterprise risk management framework 2004 (put emphasis on managerial practices of the board)
COSO 3 ICIF-2 2013 (principle-based)
COSO 4 ERMF-2 2017
COSO 5 FRMG 2015
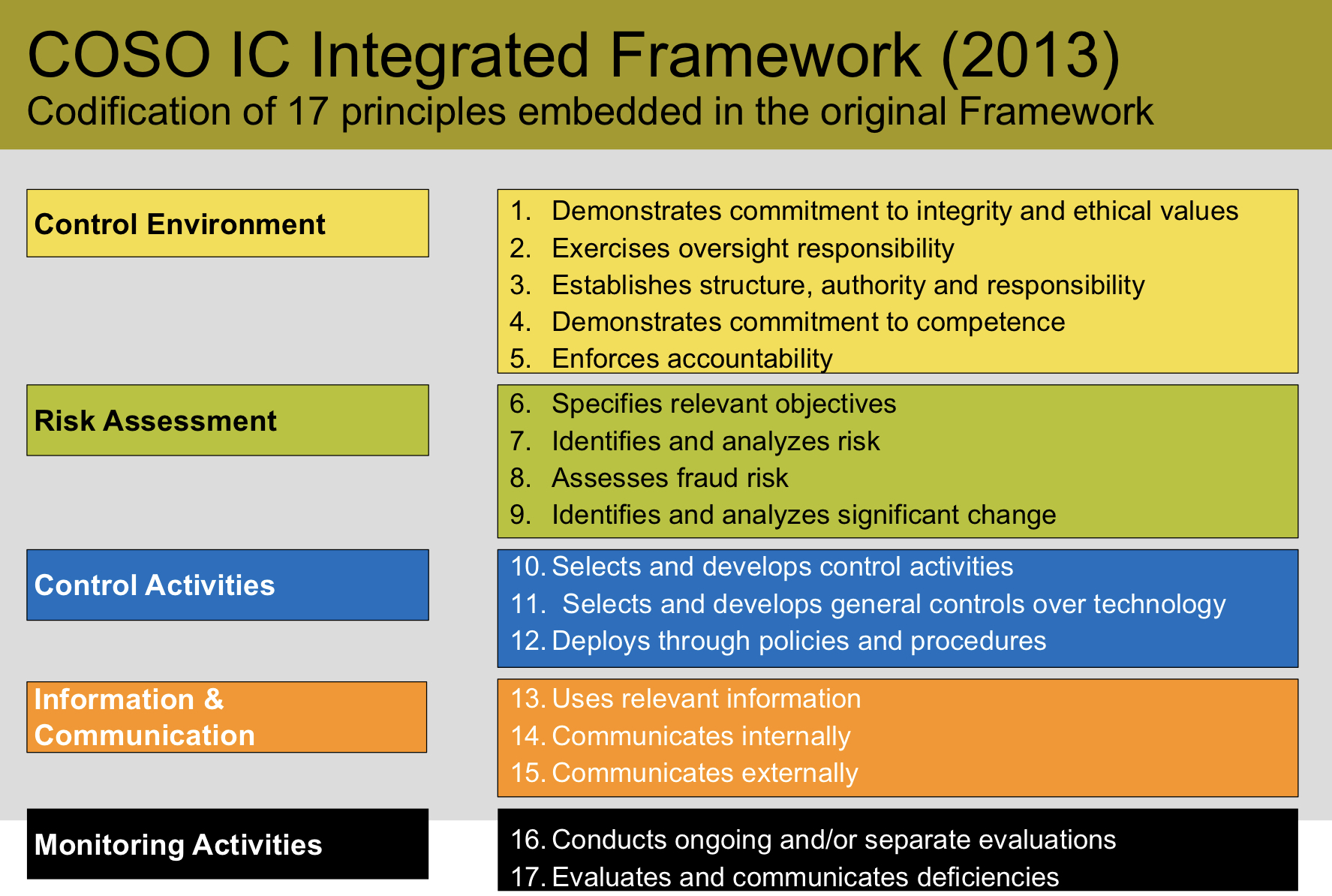
- Control environment: the basis for responsibilities, cultures and accountability.
- Risk assessment: the ability to identify threats/risks.
- Control activities: actions to mitigate risks.
- Information and communication: designed for coordination
- Monitoring: some maintenance whether processes still in operation
COSO provides reasonable but not absolute assurance. Principles give people leeway to implement, so COSO is difficult to be implemented. Principle-based definition relieves the burden of the management to achieve objectives and at the same time reduces the accountability.
Week 2 Tutorial
Definition of IC
Risk-taking is fundamental to business activities. Separation of ownership leads to increased risk for investors, who then wish for more control. Disclosure, as a part of accountability and internal control system, gives investors assurance that the company is under control.
Rule-based consists of policies and procedures where rigidly enforced compliance is needed.
Risk concept is vague.
Quantification of risks makes risk objective, and it’s the problem in COSO model. Risks are difficult to quantify.
Heineken Annual Report
Heineken pretended to be in control.

In a way of negative assurance.

Week 3 Lecture
Risk approach –> pretend it can predict the future
Ulrich Beck:
- Uncertainty does not exist anymore.
- Risks can be managed in a scientific way.
COSO 2 ERMF
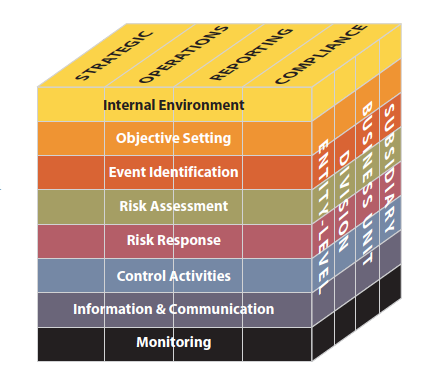
- Internal Environment – The internal environment encompasses the tone of an organization, and sets the basis for how risk is viewed and addressed by an entity’s people, including risk management philosophy and risk appetite, integrity and ethical values, and the environment in which they operate.
- Objective Setting – Objectives must exist before management can identify potential events affecting their achievement. Enterprise risk management ensures that management has in place a process to set objectives and that the chosen objectives support and align with the entity’s mission and are consistent with its risk appetite.
- Event Identification – Internal and external events affecting achievement of an entity’s objectives must be identified, distinguishing between risks and opportunities. Opportunities are channeled back to management’s strategy or objective-setting processes.
- Risk Assessment – Risks are analyzed, considering likelihood and impact, as a basis for determining how they should be managed. Risks are assessed on an inherent and a residual basis.
- Risk Response – Management selects risk responses – avoiding, accepting, reducing, or sharing risk – developing a set of actions to align risks with the entity’s risk tolerances and risk appetite.
- Control Activities – Policies and procedures are established and implemented to help ensure the risk responses are effectively carried out.
- Information and Communication – Relevant information is identified, captured, and communicated in a form and timeframe that enable people to carry out their responsibilities. Effective communication also occurs in a broader sense, flowing down, across, and up the entity.
- Monitoring – The entirety of enterprise risk management is monitored and modifications made as necessary. Monitoring is accomplished through ongoing management activities, separate evaluations, or both.
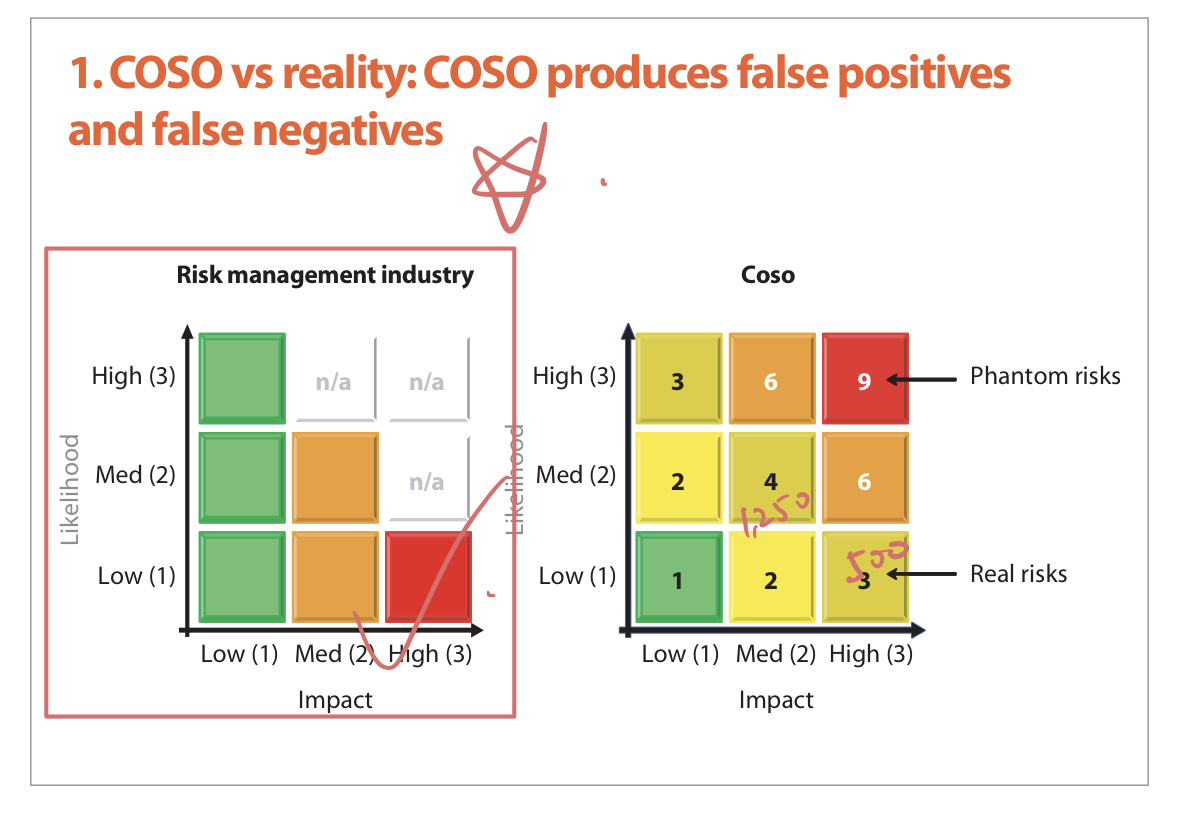
Samad Kahn: Why COSO is flawed (2005)

COSO not only fails to help a firm assess its risks, it actually obfuscates the risk assessment process.
- False-positive: Expending and intensifying control structures in areas where they are already over-controlled.
- False-negative: Completely ignoring areas of major control weakness.
Issues
- Resource-intensive – Identifying and documenting the risks in each and every process.
- The way the risk information is collected – Business managers cannot correctly assess the possibility of each risk event.
- A huge catalog of risks – difficult to prioritize
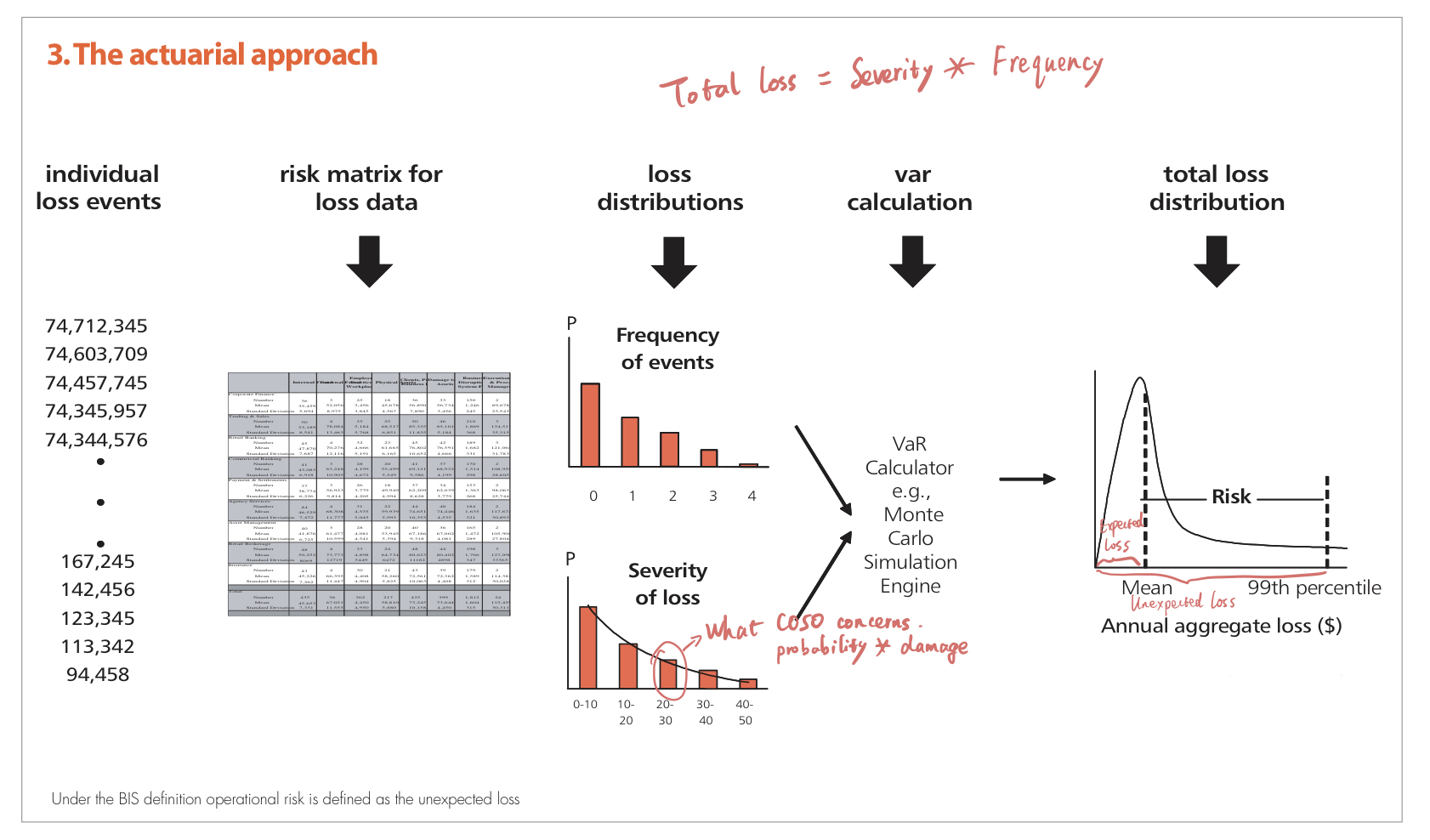
Michael Power – The risk management of nothing (2009)
Assurance is provided by audit trails.
There are conflicts in risk appetites between different parties. Risk appetite is a concept of dynamic construction. It is a challenge for senior managers to mediate different risk appetites.
The COSO’s approach to ERM leads to rule-based compliance, which is also partly the result of the rise of audit industry. Risk management should not be simplified as financial figures.
Alternatives
- Scenario analysis / scenario planning
- Business continuity management: Originated outside of accounting field; addresses the issue of interconnectedness.
Week 4 Lecture
One issue of ERM: There is no requirements for producing (useful) risk information.
W4A Pa&Sp Adoption and design of ERM in practice

Part 1
The factors explaining differences in the level of adoption
- Enforcement environment (Listed companies) but not the regulation
- Internal influence (CRO, Audit committee)
- Owner-management (Insider owners tend to less rely on ERM due to less agency problems)
- Organisation size (Larger organisations need and can afford (fully functioning) ERM)
- Financial industry (lowering the coat of capital)
Part 2
ERM design choices impacting perceived risk management effectiveness
Perceived –> Not the actual effectiveness
COSO adoption is under-estimated. (P24)
Not impacting
- COSO adoption
- Quantification of risk appetite (Tolerance) (66% not doing this)
- Lower-level management participation
- Richness of petrospective and prospective risk reporting
Impacting
- Frequency of risk assessments
- Frequency of risk reporting
- Quantification of risk assessment (COSO’s preference to quantify risks)
Conclusions
Findings challenge the validity of COSO’s key assumptions.

W4B Te&De
Noise in communication

Issues
Discursive process, time consuming, loads of information
Normally: Top-down, Higher-level management holds lower-level management into account.
ERM creates a situation that lower management (ROs) represents to higher management. When the documented risks discussed at higher levels, the documentations are modified as the higher-level managements’ desire. This creates the mutation of information and makes the information more difficult to handle at higher-level.
As ERM focuses on the corporation as a whole, individuals are not aligned to their responsibilities and focus on corporation-wide risks.
Findings
ERM is trying to document the uncertainties as accounting does with the certainties.
Individuals have different understandings about uncertainties and risks as they document risks into the system according to their own perceptions.
Individuals identify their own risks and take these risks as their responsibilities. However, the risks identified can be ‘eliminated’ by the management’s desire.
ERM makes the whole corporation focus on risks, providing more opportunities for the corporation to make changes in its operations.
ERM approach in Company X may bring benefit to the company’s operational creativity as it enables knowledge sharing, but it makes company less controllable to top managements.
W4C Sc&Pr (2014)
Organizations are not able to produce useful risk information, in the form of knowledge(?).

Findings
Risks are difficult to commensurate or compare. In other words, there is no common unit to measure risks. As a result, risks cannot be assessed objectively, and organisation knowledge generation is necessary to correctly identify and assess risks.
The risk management processes themselves can also introduce risks, which are called secondary risks. Different risks are interdependent, and the relations are difficult to identify. Organisational risk knowledge is a good way to prevent secondary risks.

W4D Bro_ea (2015)
ALL IMPORTANT NOTES FOR THIS PAPER ARE IN PAPER ITSELF.
THIS PAPER LISTS SOME FACTS ABOUT ERM, AND AT THE SAME TIME CRITICIZES IT.
MANAGERIAL RESEARCH IS NECESSARY FOR ERM.



Week 4 Tutorial
Don’t calculate (accounting perspective), but understand risk management in a managerial way.
COSO should focus on providing useful risk information and leave the decision-making responsibilities to managements.
Stories and other qualitative assurances are more useful than assurances provided by monetary figures. So forget COSO and do what should be done.
Week 5 Lecture
W5A Tr_ea_1 (2013)
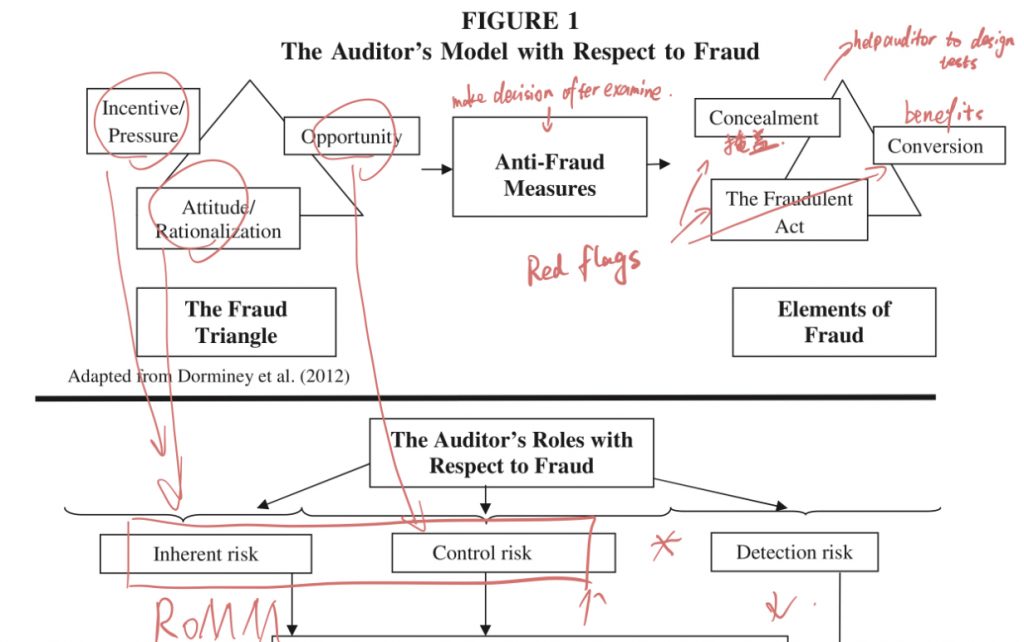
The fraud triangle is too simplistic.
- Incentives / Pressures: Money, Ideology, Coercion, Ego
- Attitude / Rationalization: Human behaviors.
- Opportunity: Internal control
- Control environment
- Control activities: In conditions of collusion and management override, activities are disabled.
- Monitoring: Whether anit-fraud measures are effective.

W5B Tr_ea_2 (2014)
PLEASE USE Ctrl-F TO SEARCH FOR ANY KEY POINT IN PDFs.


W5C Mu&Da (2011)
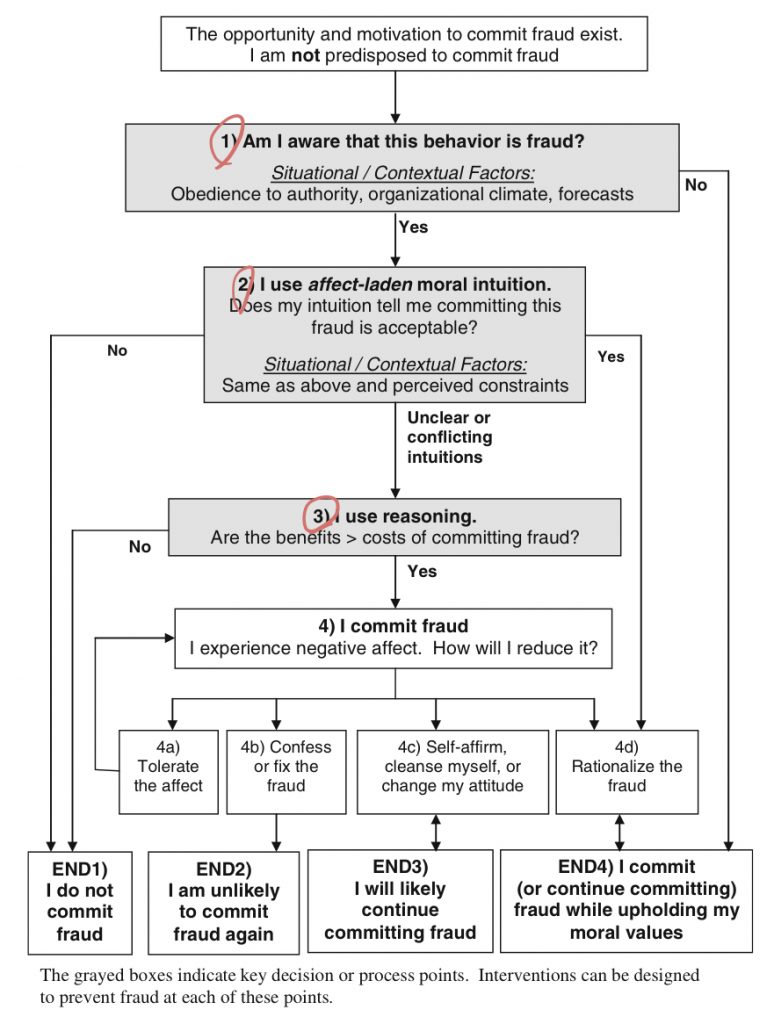
- Lack of awareness: Do not recognize that the behavior is fraudulent.
- Intuition acceptable 直觉: Rationalization is the mechanism used to avoid negative affect (feeling)
- Reasoning 纠结: More slowly, weighs between benefits and costs.
1 Insidious situations: Obedience, Organisational climate, Forecasts
Week 6 Lecture
W6A Power (2013)
W6B McShane (2017)
W6C Viscelli et al. (2016)

发表评论